Privacy Policy for managementimplementation.blogspot.com
If you require any more information or have any questions about our privacy policy, please feel free to contact us by email at pulauputri32@gmail.com.
At managementimplementation.blogspot.com, the privacy of our visitors is of extreme importance to us. This privacy policy document outlines the types of personal information is received and collected by managementimplementation.blogspot.com and how it is used.
Log Files
Like many other Web sites, managementimplementation.blogspot.com makes use of log files. The information inside the log files includes internet protocol ( IP ) addresses, type of browser, Internet Service Provider ( ISP ), date/time stamp, referring/exit pages, and number of clicks to analyze trends, administer the site, track user’s movement around the site, and gather demographic information. IP addresses, and other such information are not linked to any information that is personally identifiable.
Cookies and Web Beacons
managementimplementation.blogspot.com does use cookies to store information about visitors preferences, record user-specific information on which pages the user access or visit, customize Web page content based on visitors browser type or other information that the visitor sends via their browser.
DoubleClick DART Cookie
.:: Google, as a third party vendor, uses cookies to serve ads on managementimplementation.blogspot.com.
.:: Google's use of the DART cookie enables it to serve ads to users based on their visit to managementimplementation.blogspot.com and other sites on the Internet.
.:: Users may opt out of the use of the DART cookie by visiting the Google ad and content network privacy policy at the following URL - http://www.google.com/privacy_ads.html
Some of our advertising partners may use cookies and web beacons on our site. Our advertising partners include ....
Google Adsense
These third-party ad servers or ad networks use technology to the advertisements and links that appear on managementimplementation.blogspot.com send directly to your browsers. They automatically receive your IP address when this occurs. Other technologies ( such as cookies, JavaScript, or Web Beacons ) may also be used by the third-party ad networks to measure the effectiveness of their advertisements and / or to personalize the advertising content that you see.
managementimplementation.blogspot.com has no access to or control over these cookies that are used by third-party advertisers.
You should consult the respective privacy policies of these third-party ad servers for more detailed information on their practices as well as for instructions about how to opt-out of certain practices. managementimplementation.blogspot.com's privacy policy does not apply to, and we cannot control the activities of, such other advertisers or web sites.
If you wish to disable cookies, you may do so through your individual browser options. More detailed information about cookie management with specific web browsers can be found at the browsers' respective websites.
Friday, August 20, 2010
Professional Services
MSA's professional services staff uses rigorous, field-tested, standard-setting methodologies and extensive hands-on experience. We advise our customers on how to architect and implement an enterprise management operation that succeeds in meeting their business mission and protects enterprise network assets. Today's enterprise networks are a crucial asset for many businesses, involving data, telecommunications, and converged media sources.
The result is a system that delivers the reliability, scalability, usability, accuracy, and maintainability to meet the competitive challenges our customers face. What does a typical enterprise management system delivered by MSA look like? Take a look at this.
Free Executive level overview of Earned Value Management
Pinnacle is pleased to offer a free Executive level overview of Earned Value Management Implementation for organizations that are facing new or changing EVM requirements.
This presentation has been extremely effective at building Executive buy-in and Adoption of Earned Value Management.
The presentation is intended for CEO, CFO, Program Managers and EVM Implementation teams. We will arrange a presentation for your company and configure the presentation to fit your specific needs based on contract type, client Agency and current Project Management infrastructure .
We have had excellent reviews from companies who are:
This presentation has been extremely effective at building Executive buy-in and Adoption of Earned Value Management.
The presentation is intended for CEO, CFO, Program Managers and EVM Implementation teams. We will arrange a presentation for your company and configure the presentation to fit your specific needs based on contract type, client Agency and current Project Management infrastructure .
We have had excellent reviews from companies who are:
- Facing new EVM mandates in their contract requirements
- Evaluating Earned Value Management and Project Management software.
- Dealing with increased EVM rigor, IBRs or EVMS validations
- Looking at implementing EVM to help in responding to RFPs and winning new contracts
- Not sure how implementing EVM will impact their organizations
The content of the presentation can be tailored to suit your specific requirements, as dictated by your organizational or contractual needs. All we ask is that you assemble a team of decision makers and implementation stakeholders. We typically have a preliminary conversation to determine your specific goals, and then we deliver a 1-2 hour presentation to your team.
The standard outline of the presentation includes:
Overview of Earned Value Management (EVM)
- EVM concepts and terminology
- EVM Principles and Integrated Program Management (IPM)
Government Reviews and Validation – As required by specific Agencies
- EVM Mandate Thresholds and the different level of EVM requirements (ex. 32 ANSI criteria versus 10 core criteria)
- EVM Validation process and timeframes
- Integrated Baseline Reviews
Elements of an effective EVMS
- People, Process, Tools, Deliverables
- Software System overview
Competency management implementation guide
The ITG Competency Management Implementation Guide offers tested methods, tools and guidance for customizing the ITG Model and other competency data to fit the organization’s culture, and for implementing it on a sustainable basis into your competency-based workforce initiative.
The Competency Management Implementation Guide (IMPG) documents the combined experiences of our competency consultants and the clients with whom they’ve worked. It offers a variety of tools: tutorials, a project plan, document templates, meeting agendas, facilitation guides, best practices, PowerPoint slides and others. It underscores Salary.com’s ability to assist in rapid implementation of a competency-based workforce initiative.
The IMPG documents our phased implementation approach and focuses on:
• Ensuring that the jobs and competencies required to achieve the organization’s desired future are clearly defined and in lock step with business plans and directions.
• Providing individuals with information on competencies required for success in the organization’s various job functions.
• Providing individuals and managers with actionable information on current competencies and the gaps that may exist between the competencies that are currently on hand and those which are required for the future.
• Providing individuals and managers with actionable information on current competency strengths.
• Providing both individual and organizational development plans to close selected gaps and take full advantage of strengths.
• Ensuring that competency data is properly maintained for use beyond the initial project and the demands of the moment.
Telecom & Mobility Management Implementation Project Tips
I was recently reading AOTMP's State of the Industry Report on the Telecom Expense and Wireless Expense Management Industry. You can find it here There was some interesting feedback from clients who have engaged in TEM projects. There was one question in particular that resonated with me.
"If there was one thing you would do differently with your TEM program, what would it be? "
Some of the respondents regretted their approach to their project. This got me thinking...... what advice do we typically give so that there are no regrets? We are asked daily for suggestions on how to ensure a TEM/WEM initiative is successful. The following tips may help you start off on the right foot.
Tip #1 - Give everyone a heads up - TEM projects require change...change that sometimes scares people. The more buy-in and comfort you can secure from the groups involved, the quicker and more effectively your program will be implemented. Lay out the key organizational goals and the reasons why certain tasks must be done. If this is clearly communicated in terms of those that stand to benefit from the solution - cooperation and enthusiasm should be strong.
Tip #2 - Start gathering your info NOW - Getting your arms around your inventory and billing can sometimes be a pain. No matter who you choose, most vendors will ask for very similar information, so you benefit regardless of who you select. Even put aside a box in your office or a folder on your desktop and start adding bills and records that you think may be useful when the time comes Telecom management project plan
Tip #3 - Dedicate resources to the project - One of the biggest reasons that an implementation is delayed is due to insufficient resources. It is important to prepare all of the groups involved and clearly define who responsible for what tasks and share this information with the vendor you choose. If a vendor recommends a specific headcount, trust them. They typically know how many man-hours tasks will take.
Tip #4 - Speak up and discuss expectations - Of course this applies to the vendor but it also applies to you. There are certain areas that are MUST tackle subjects. For example, project timeframes, internal goals, expectations, target dates should NEVER be assumed. Any client engagement should start with a project initiation meeting where timeframes are mutually developed, mapped and signed off on by both you and the vendor. Schedule a discovery session ...it will be worth your time.
Tip #5 - Clearly define the scope of work. -The more information you can gather regarding the scope, the better. Again, this is another area that must be clearly discussed and outlined with your vendor. The scope of work should be clearly defined and mutually agreed upon. A plan should also be discussed and mapped out that cover how to handle out of scope issues that arise during the engagement.
"If there was one thing you would do differently with your TEM program, what would it be? "
Some of the respondents regretted their approach to their project. This got me thinking...... what advice do we typically give so that there are no regrets? We are asked daily for suggestions on how to ensure a TEM/WEM initiative is successful. The following tips may help you start off on the right foot.
Tip #1 - Give everyone a heads up - TEM projects require change...change that sometimes scares people. The more buy-in and comfort you can secure from the groups involved, the quicker and more effectively your program will be implemented. Lay out the key organizational goals and the reasons why certain tasks must be done. If this is clearly communicated in terms of those that stand to benefit from the solution - cooperation and enthusiasm should be strong.
Tip #2 - Start gathering your info NOW - Getting your arms around your inventory and billing can sometimes be a pain. No matter who you choose, most vendors will ask for very similar information, so you benefit regardless of who you select. Even put aside a box in your office or a folder on your desktop and start adding bills and records that you think may be useful when the time comes Telecom management project plan
Tip #3 - Dedicate resources to the project - One of the biggest reasons that an implementation is delayed is due to insufficient resources. It is important to prepare all of the groups involved and clearly define who responsible for what tasks and share this information with the vendor you choose. If a vendor recommends a specific headcount, trust them. They typically know how many man-hours tasks will take.
Tip #4 - Speak up and discuss expectations - Of course this applies to the vendor but it also applies to you. There are certain areas that are MUST tackle subjects. For example, project timeframes, internal goals, expectations, target dates should NEVER be assumed. Any client engagement should start with a project initiation meeting where timeframes are mutually developed, mapped and signed off on by both you and the vendor. Schedule a discovery session ...it will be worth your time.
Tip #5 - Clearly define the scope of work. -The more information you can gather regarding the scope, the better. Again, this is another area that must be clearly discussed and outlined with your vendor. The scope of work should be clearly defined and mutually agreed upon. A plan should also be discussed and mapped out that cover how to handle out of scope issues that arise during the engagement.
Facility Management
Better service management through consolidation of applications
RightStar’s facilities management implementation reduces operating costs by consolidating several facility and administrative applications using BMC Service Desk Express or BMC Remedy as the application centerpiece. Potential facilities applications include:
RightStar enables organizations to make better use of their existing service management tools and processes by reducing, rather than increasing, the number of applications and systems supported.
Identity Management (IdM)
First Soft Solutions Long experience helping global companies meet business challenges is at the core of First Soft Solutions’s Identity Management Practice. First Soft Solutions has been helping customers worldwide realize maximum value from their Identity Management implementations. We delivers Identity Management consulting, Identity Management implementation, Identity Management integration and post implementation services for our customers.
First Soft Solutions’s Identity Management Support services cover the entire Identity Management systems spectrum — spanning from configuration set up, customization/enhancement of existing functionality, and post implementation support.
Our proven Identity Management integration capability enables seamlessly integrated solutions that increase the value of technology investments.
First Soft Solutions maintains a resource pool of experienced professionals, consultants, solution designers and developers. This high caliber staff is backed by proven end-to-end project execution methodologies. First Soft Solutions’s focused Delivery Center and skilled resource pool ensures scalability, while a well-established onsite-offshore execution model delivers cost effective solutions for clients.
First Soft Solutions provides consulting, integration and managed services for the following Identity Management technologies:
Our proven Identity Management integration capability enables seamlessly integrated solutions that increase the value of technology investments.
First Soft Solutions maintains a resource pool of experienced professionals, consultants, solution designers and developers. This high caliber staff is backed by proven end-to-end project execution methodologies. First Soft Solutions’s focused Delivery Center and skilled resource pool ensures scalability, while a well-established onsite-offshore execution model delivers cost effective solutions for clients.
First Soft Solutions provides consulting, integration and managed services for the following Identity Management technologies:
- Automated Provisioning
- Password Management
- Compliance Management
- Role Management
- Enterprise Single Sign-On
- Centralized Unix Authentication
- Privileged Access Management
- Virtual Directory/Metadirectory
- Web Access Management
Implementation & Support Services
For end-to-end transformation of the supply chain, we provide services in the following areas:
We assist our clients in custom solution implementation. The service comprises of doing a requirement gathering & gap analysis and customizing solutions as per the customer needs. We finalize implementation road map, implement pilot, rollout solution, and review performance. The implementation is supported with training and documentation, key learning's review and project closure. During the whole custom implementation, special focus is given on managing change.
We leverage the blended onsite/offshore model for Application Maintenance & Support services. Our services encompass activities such as:
We offer services for managing the following processes for our clients:
To successfully cater to client needs, we complement our service offerings with in-depth expertise in Supply Chain products from almost all the leading players such as SAP, Oracle, i2, Manhattan Associates, Manugistics and JDA.
- Package Implementation & Roll-Out
We assist our clients in end-to-end package implementation of supply chain management applications. The service comprises a comprehensive program on requirement analysis, executed through interactive workshop with the application users and process consultants. The program is followed by global design, product configuration, testing and post go-live support. We adopt industry best practices, take advantage of the implementation and rollout methodology and use the rollout kit to help reduce the implementation cycle time.
- Custom Solution Implementation
We assist our clients in custom solution implementation. The service comprises of doing a requirement gathering & gap analysis and customizing solutions as per the customer needs. We finalize implementation road map, implement pilot, rollout solution, and review performance. The implementation is supported with training and documentation, key learning's review and project closure. During the whole custom implementation, special focus is given on managing change.
- Application Maintenance & Support
We leverage the blended onsite/offshore model for Application Maintenance & Support services. Our services encompass activities such as:
- Multiple support window (After business hours, select-hours, or 24x7 support services)
- Support Services by phone, email, fax and pager
- Multiple level support (L1, L2 and L3 Support)
- Quality Assurance Testing
- Tools driven Application Support using PMSmart (Ticket Tracking System)
- Supply Chain BPO
We offer services for managing the following processes for our clients:
- Procure-to-Pay, which includes purchase order processing (transactions), e-catalog management, RMA management, material expediting, vendor relationship management and vendor A/C payables management.
- Order-to-Cash, which includes sales order processing (transactions), order fulfillment, RMA management, material supply co-ordination, inventory management, customer – A/C receivables management, and data master administration.
- Master data creation and maintenance of material and vendor data.
To successfully cater to client needs, we complement our service offerings with in-depth expertise in Supply Chain products from almost all the leading players such as SAP, Oracle, i2, Manhattan Associates, Manugistics and JDA.
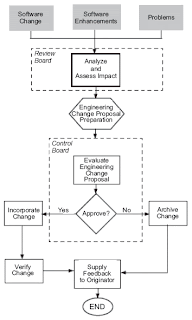
Configuration Management Fundamentals
Change is a constant feature of software development. To eliminate change is to remove the opportunities to take advantage of lessons learned, to incorporate advancing technology, and to better accommodate a changing environment. Refusal to incorporate change can mean system limitations and early obsolescence, which, in the world of technology, can sign your system's death certificate before it is born. However, change is not universally benign and must be controlled in its introduction to a project.
All projects change something. As a project is executed, changes to the initial project plan and products are a natural occurrence. The following are common sources of changes:
All projects change something. As a project is executed, changes to the initial project plan and products are a natural occurrence. The following are common sources of changes:
- Requirements. The longer the delivery cycle, the more likely they will change.
- Changes in funding.
- Technology advancements.
- Solutions to problems.
- Scheduling constraints.
- Customer expectations.
- Serendipitous (unexpected) opportunities for an improved system.
Some of these changes may appear as options while others may be mandated from above or by circumstance, as in the loss of funding. While all progress is accompanied by change, not all change is indicative of progress. If not properly handled, change can slip the schedule, affect the quality, and even kill the project. As a project draws closer to its completion, the impacts of change are more severe [1]. Clearly, a mechanism is needed to control change.
In software development and other projects, proposed changes must be evaluated to determine their overall contribution to the project goals. Do they lead to improvements or do they ultimately impede or lower project quality? Even those changes that are ultimately beneficial must be controlled in their introduction and implementation.
Putting a bigger engine in a plane may improve its capabilities, but it cannot be implemented until the aircraft's structure has been found capable or been upgraded to support the increased weight and thrust.
Configuration management (CM) is the process of controlling and documenting change to a developing system. It is part of the overall change management approach. As the size of an effort increases, so does the necessity of implementing effective CM. It allows large teams to work together in a stable environment while still providing the flexibility required for creative work [2]. CM in a software environment is an absolute necessity. CM has three major purposes [1]:
- Identify the configuration of the product at various points in time.
- Systematically control changes to the configuration.
- Maintain the integrity and traceability of the configuration throughout the product life cycle.
CM accomplishes these purposes by answering and recording the answers to the change questions: who, what, when, and why, shown in Figure 1 [1]. Being able to answer these questions is a sign of effective CM.
Figure 1: Configuration Management Questions
Effective CM provides the following essential benefits to a project:
In short, CM can provide cost effective project insurance when properly planned, organized, and implemented. It must be integral to your overall project execution, and to your charter/customer agreement. Proposed changes must be dealt with systematically, promptly, and honestly [1]. If the CM process is unreasonable or unresponsive, people will try to circumvent the process, leading to chaos and a loss of the benefits of true CM.
Effective CM provides the following essential benefits to a project:
- Reduces confusion and establishes order.
- Organizes the activities necessary to maintain product integrity.
- Ensures correct product configurations.
- Limits legal liability by providing a record of actions.
- Reduces life-cycle costs.
- Enables consistent conformance with requirements.
- Provides a stable working environment.
- Enhances compliance with standards.
- Enhances status accounting.
In short, CM can provide cost effective project insurance when properly planned, organized, and implemented. It must be integral to your overall project execution, and to your charter/customer agreement. Proposed changes must be dealt with systematically, promptly, and honestly [1]. If the CM process is unreasonable or unresponsive, people will try to circumvent the process, leading to chaos and a loss of the benefits of true CM.
Process Description
While CM is a major element of a change control program, it is such a multifaceted discipline that it should be considered not simply as another activity, but as a program in and of itself. Establishing an effective CM program requires an understanding of CM functions and of the overall CM process.
Functions of Configuration Management
CM is comprised of four primary functions: identification, change control, status accounting, and auditing. These are shown in Figure 2, along with their subfunctions. All CM activity falls within the bounds of these functions.
CM is comprised of four primary functions: identification, change control, status accounting, and auditing. These are shown in Figure 2, along with their subfunctions. All CM activity falls within the bounds of these functions.
Identification
This function identifies those items whose configuration needs to be controlled, usually consisting of hardware, software, and documentation. These items would probably include such things as specifications, designs, data, documents, drawings, software code and executables, components of the software engineering environment (compilers, linkers, loaders, hardware environment, etc.), and hardware components and assemblies. Project plans and guiding documents should also be included, especially the project requirements. A schema of names and numbers is developed for accurately identifying products and their configuration or version level. This must be done in accordance with project identification requirements. Finally, a baseline configuration is established for all configuration items and systems. Any changes to the baseline must be with the concurrence of the configuration control organization [2].
Although key components to be managed are requirements and source code, related documentation and data should be identified and placed under CM control. It is important to store and track all environment information and support tools used throughout the software life cycle to ensure that the software can be reproduced. Table 1 lists examples of items typically put under CM control.
Table 1: Items Under CM Control
Change Control
Configuration control establishes procedures for proposing or requesting changes, evaluating those changes for desirability, obtaining authorization for changes, publishing and tracking changes, and implementing changes. This function also identifies the people and organizations who have authority to make changes at various levels (configuration item, assembly, system, project, etc.,) and those who make up the configuration control board(s) (CCB). (According to IEEE 610.12 [3], a CCB is a group of people responsible for evaluating and approving or disapproving proposed changes to configuration items, and for ensuring implementation of approved changes.)
Additionally, various change criteria are defined as guidelines for the control organizations. Different types of configuration items or different systems will probably need different control procedures and involve different people. For example, software configuration control has different needs and involves different people than communications configuration control and would probably require different control rules and a different control board [2]. Configuration change control activities include the following:
- Defining the change process.
- Establishing change control policies and procedures.
- Maintaining baselines.
- Processing changes.
- Developing change report forms.
- Controlling release of the product.
Figure 3: Generic Change Process [5]
Status Accounting
Status accounting is the documentation function of CM. Its primary purpose is to maintain formal records of established configurations and make regular reports of configuration status. These records should accurately describe the product, and are used to verify the configuration of the system for testing, delivery, and other activities. Status accounting also maintains a history of change requests and authorizations, along with status of all approved changes. This includes the answers to the CM questions in Figure 1 [2].
Key information about the project and configuration items can be communicated to project members through status accounting. Software engineers can see what fixes or files were included in which baseline. Project managers can track completion of problem reports and various other maintenance activities. Minimal reports to be completed include transaction log, change log, and item delta report. Other typically common reports include resource usage, stock status (status of all configuration items), changes in process, and agreed-upon deviations [6].
Auditing
Effective CM requires regular evaluation of the configuration. This is done through the auditing function, where the physical and functional configurations are compared to the documented configuration. The purpose of auditing is to maintain the integrity of the baseline and release configurations for all controlled products [2]. Auditing is accomplished via both informal monitoring and formal reviews.
Configuration auditing verifies that the software product is built according to the requirements, standards, or contractual agreement. Test reports and documentation are used to verify that the software meets the stated requirements. The goal of a configuration audit is to verify that all software products have been produced, correctly identified and described, and that all change requests have been resolved according to established CM processes and procedures. Informal audits are conducted at key phases of the software life cycle.
There are two types of formal audits that are conducted before the software is delivered to the customer: Functional Configuration Audit (FCA) and Physical Configuration Audit (PCA). FCA verifies that the software satisfies the software requirements stated in the System Requirements Specification and the Interface Requirements Specification. In other words, the FCA allows you to validate the system against the requirements. The PCA determines whether the design and reference documents represent the software that was built. Configuration audit answers the questions, "Does the system satisfy the requirements?" "Are all changes incorporated in this version?" Configuration audit activities include the following:
- Defining audit schedule and procedures.
- Identifying who will perform the audits.
- Performing audits on established baselines.
- Generating audit reports.
Establishing a Software Baseline Library
In support of the above activities, a software baseline library is established. The library is the heart of the CM system. It serves as the repository for the work products created during the software life cycle. Changes to baselines, and the release of software products, are systematically controlled via the change control and configuration auditing functions. The software library provides the following:
- Supports multiple control levels of Software Configuration Management (SCM).
- Provides for the storage and retrieval of configuration items or units.
- Provides for the sharing and transfer of configuration items or units between control levels within the library.
- Provides for the storage and recovery of archive versions of configuration items or units.
- Helps to ensure correct creation of products from the software baseline library.
- Provides storage, update, and retrieval of CM records.
- Supports production of CM reports.
- Provides for maintenance of library structure [7].
In the past, libraries have been composed of documentation on hard copy and software on machine-readable media. Today, with the advances in information technology and standards that encourage contractors to use automated processing and electronic submittal techniques, organizations are moving toward maintaining all information on machine-readable media.
Configuration Management Process
Understanding what CM is supposed to accomplish is one thing. Putting it into practice is another. As with most project activities, CM begins with planning. With a plan, configuration baselines can be established. Following this initial configuration identification, the cyclical configuration control process is put into motion. These three major CM implementation activities are shown in Figure 4.
Figure 4: Configuration Management Implementation Process
Planning
Planning begins by defining the CM process and establishing procedures for controlling and documenting change. A crucial action is the designation of members of the CCB. Members should be chosen who are directly or indirectly involved or affected by changes in configuration. For example, a software CCB would obviously be populated with representatives from different software teams, but software affects many more aspects of a project. There should also be representatives from the hardware, test, systems, security, and quality groups as well as representatives from project management and possible other organizations.
Not all changes would be reviewed by this august body. Changes occur at different system levels and affect different portions of the overall system. Many changes will probably only affect a small subset of the system and could therefore be reviewed and approved by a smaller group. Some sort of delineation of change levels should be made during planning to keep change decisions at the proper level. While software CM is essential, there may need to be other CCBs to control change in other areas of the project. Again, this is something that should be worked out in the planning phase. Various software tools exist that can facilitate the CM process flow and maintain configuration history. Using a CM software tool is highly recommended. The temptation will be to choose a tool because it looks good in a demonstration and then build the CM process around it. The process should be defined first, and then a tool chosen to facilitate the process.
Establishing Baselines
Once the CM program exists on paper, it must be determined just what configurations it will control. The second major step of implementing effective CM is identifying what items, assemblies, code, data, documents, systems, etc. will fall under configuration control. With the configuration items identified, the baseline configuration must be identified for each item. For items that already exist, it may prove to be nothing more than examining or reviewing and then documenting. For those items that have not been developed yet, their configuration exists in the requirements database or in the project plans. Until they come into physical or software reality, changes to their configuration will consist only of changes to the requirements or plans.
Another essential activity in this step is developing a schema of numbers, letters, words, etc. to accurately describe the configuration revision, or version, for each general type of configuration item. There may be project requirements that dictate some type of nomenclature, or there may be an organizational or industry standard that can be used as the basis for configuration identification.
Controlling, Documenting, and Auditing
When the baselines have been established, the challenge becomes one of keeping the actual and documented configurations identical. Additionally, these baselines must conform to the configuration specified in the project requirements. This is an iterative process consisting of the four steps shown in Figure 4.
All changes to the configuration are reviewed and evaluated by the appropriate configuration control representatives specified in the CM plan. The change is either approved or disapproved. Both approvals and disapprovals are documented in the CM history. Approved changes are published and tracked or monitored until they are implemented. The appropriate configuration baseline is then updated, along with all other applicable documents, and reports are published and sent to affected organizations indicating the changes that have occurred. At selected time intervals and whenever there appears to be a need, products and records are audited to ensure the following:
Planning begins by defining the CM process and establishing procedures for controlling and documenting change. A crucial action is the designation of members of the CCB. Members should be chosen who are directly or indirectly involved or affected by changes in configuration. For example, a software CCB would obviously be populated with representatives from different software teams, but software affects many more aspects of a project. There should also be representatives from the hardware, test, systems, security, and quality groups as well as representatives from project management and possible other organizations.
Not all changes would be reviewed by this august body. Changes occur at different system levels and affect different portions of the overall system. Many changes will probably only affect a small subset of the system and could therefore be reviewed and approved by a smaller group. Some sort of delineation of change levels should be made during planning to keep change decisions at the proper level. While software CM is essential, there may need to be other CCBs to control change in other areas of the project. Again, this is something that should be worked out in the planning phase. Various software tools exist that can facilitate the CM process flow and maintain configuration history. Using a CM software tool is highly recommended. The temptation will be to choose a tool because it looks good in a demonstration and then build the CM process around it. The process should be defined first, and then a tool chosen to facilitate the process.
Establishing Baselines
Once the CM program exists on paper, it must be determined just what configurations it will control. The second major step of implementing effective CM is identifying what items, assemblies, code, data, documents, systems, etc. will fall under configuration control. With the configuration items identified, the baseline configuration must be identified for each item. For items that already exist, it may prove to be nothing more than examining or reviewing and then documenting. For those items that have not been developed yet, their configuration exists in the requirements database or in the project plans. Until they come into physical or software reality, changes to their configuration will consist only of changes to the requirements or plans.
Another essential activity in this step is developing a schema of numbers, letters, words, etc. to accurately describe the configuration revision, or version, for each general type of configuration item. There may be project requirements that dictate some type of nomenclature, or there may be an organizational or industry standard that can be used as the basis for configuration identification.
Controlling, Documenting, and Auditing
When the baselines have been established, the challenge becomes one of keeping the actual and documented configurations identical. Additionally, these baselines must conform to the configuration specified in the project requirements. This is an iterative process consisting of the four steps shown in Figure 4.
All changes to the configuration are reviewed and evaluated by the appropriate configuration control representatives specified in the CM plan. The change is either approved or disapproved. Both approvals and disapprovals are documented in the CM history. Approved changes are published and tracked or monitored until they are implemented. The appropriate configuration baseline is then updated, along with all other applicable documents, and reports are published and sent to affected organizations indicating the changes that have occurred. At selected time intervals and whenever there appears to be a need, products and records are audited to ensure the following:
- The actual configuration matches the documented configuration.
- The configuration is in conformance with project requirements.
- Records of all change activity are complete and up-to-date.
Updating the CM Process
It is unlikely a perfect CM program will be assembled during the initial planning stage. There will be learning and changes in the program that indicate a need for adjustments in the CM process. These may be any mixture of modifications to make it more efficient, responsive, or accurate. When changes in the CM process are needed, consider them as you would any other changes, get the approval of all participating organizations, and implement them as appropriate. It would be ironic indeed to have an unchanging change process.
Configuration Management Checklist
This checklist is provided to assist you in establishing an effective CM program. If you cannot answer a question affirmatively, you should carefully examine the situation and take appropriate action.
This checklist is provided to assist you in establishing an effective CM program. If you cannot answer a question affirmatively, you should carefully examine the situation and take appropriate action.
CM Planning
___ Have you planned and documented a configuration management process?
___ Have you identified CCB members for each needed control board?
___ Has CM software been chosen to facilitate your CM process?
Establishing Baselines
___ Have all configuration items been identified?
___ Have baselines been established for all configuration items?
___ Has a descriptive schema been developed to accurately identify configuration items and changes to their configuration?
Controlling, Documenting, and Auditing
___ Is there a formal process for documenting and submitting proposed changes?
___ Is the CCB active and responsible in evaluating and approving changes?
___ Is there a higher authority to appeal to when the CCB gets hung , and cannot come to a consensus?
___ Are all changes tracked until they are fully implemented?
___ Are all changes fully documented in the baseline documents and change histories?
___ Are regular reports and configuration updates published and distributed to interested organizations?
___ Are regular audits and reviews performed to evaluate configuration integrity?
___ Are configuration errors dealt with in an efficient and timely manner?
Updating the Process
___ Is the CM program itself — its efficiency, responsiveness, and accuracy — evaluated regularly?
___ Is the CM program modified to include recommended improvements when needed?
Case Studies
The following case studies outline specific instances where organizations successfully implemented software CM (SCM).
Selecting a CM Tool
At a large aerospace corporation in the Southeast, the CM manager turned in a recommendation to purchase a CM automated tool that would satisfy all requirements identified by the CM groups. Management delayed acting on the recommendation to give the other engineering departments time to review the recommended tool.
In the end, the recommendation to purchase the tool was cancelled. It was felt that while the tool did support the CM organization, it did not adequately address other developmental considerations that the engineering ranks felt were important. Sometime later a different tool was purchased, one that satisfied all the major requirements of SCM, the software developers, SQA, test, integration, and management organizations.
Overcoming Barriers to SCM
During a recent visit to a private-sector corporation (i.e., they did not deal with government contracts) in New England, it was discovered that the developer's major concern about implementing CM activities was all the restrictions they would have to deal with. They had been led to believe that CM meant formal controls, restricted access, limited ability to apply creative solutions, and so on. When it was suggested that data can transition to formally controlled baselines through a series of informal control steps, and that CM did not mean a lockdown and bottleneck, they became eager to be involved. After a number of meetings, a phased approach to formal CM allowed for the placement of informal controls and data gathering which led to baselined items. Everyone was pleased with the process.
The developers soon realized they could work together with CM as a team to solve problems rather than as two separate organizations with their own concerns and desired solutions. More importantly, perhaps, the CM group learned that when they got out of their corner office and out onto the engineering floor (being support and service oriented) they quickly became an integral part of the engineering and development process and team.
Implementing CM With an Electronic Database
A team of 35 to 40 developers was developing six computer software configuration items, which all had two or more customer variants as well as maintenance variants. The operating system was Unix, and the development languages were Ada, C, and C++. Implementing classical CM in this type of environment would normally require three to four CM practitioners to handle all the code and document manipulations. The team chose instead to implement a mostly developerexecuted CM system called Effective SCM . They implemented a Software Query Language-compliant, database driven, process oriented CM system, which supports a rule-based, closed-loop, changepackage approach to development.
Daily interaction with the CM system by the developers provided 100 percent tracking and status accounting of everything that happened to any file in the systems without the need for intrusion or interference by CM practitioners. The CM practitioners maintained the process model and performed the configured builds. As a result, CM support to this team was less than one person, and in fact was in the order of 80-120 hours per month instead of the more than 400 hours per month that a classical approach would have used.
The electronic database created by the engineers completely documented the execution of their software development plan. It also tracked the history of every file used in the system including change documents, baselines, and releases for each file. Note that rule-based, closedloop change control electronically implemented business rules that prevented the creation of a new version without authorization and prevented closure of a change request that had not been implemented.
A change-package approach supports electronic creation of new baselines by application of changes to a previous baseline. The tool electronically adds, replaces, or removes files that are related to the list of changes being made and is very effective in tracking development activities. (Note that Effective SCM is an unregistered trademark of BOBEV Consulting. For a complete description, see "Effective Software Configuration Management" in CrossTalk February 1998.)
Lessons Learned
The following are just a sample of the many lessons that have been learned from applying CM and its associated technologies.
The Importance of Planning
With only a few exceptions, if you look at any of the CM standards, manuals, guides, books, etc., you will likely find that CM has four major functions: (1) identification, (2) change control, (3) status accounting, and (4) auditing. In nearly every case, planning is left out. Yet, SCM is using much more complex equipment to establish and maintain complex environments, multiple baselines, multiple environments on multiple platforms, etc. Like everyone else, CM has to do all that faster, cheaper, smarter, and better than before. Planning has become more important than ever.
Planning cannot be interpreted as meaning a CM Plan has been written . That is certainly a good start, but much more is needed than just a document that explains SCM's roles and responsibilities. CM planning activities must also include, to name only a few, such things as the following:
The most significant lessons are the following:
___ Have you planned and documented a configuration management process?
___ Have you identified CCB members for each needed control board?
___ Has CM software been chosen to facilitate your CM process?
Establishing Baselines
___ Have all configuration items been identified?
___ Have baselines been established for all configuration items?
___ Has a descriptive schema been developed to accurately identify configuration items and changes to their configuration?
Controlling, Documenting, and Auditing
___ Is there a formal process for documenting and submitting proposed changes?
___ Is the CCB active and responsible in evaluating and approving changes?
___ Is there a higher authority to appeal to when the CCB gets hung , and cannot come to a consensus?
___ Are all changes tracked until they are fully implemented?
___ Are all changes fully documented in the baseline documents and change histories?
___ Are regular reports and configuration updates published and distributed to interested organizations?
___ Are regular audits and reviews performed to evaluate configuration integrity?
___ Are configuration errors dealt with in an efficient and timely manner?
Updating the Process
___ Is the CM program itself — its efficiency, responsiveness, and accuracy — evaluated regularly?
___ Is the CM program modified to include recommended improvements when needed?
Case Studies
The following case studies outline specific instances where organizations successfully implemented software CM (SCM).
Selecting a CM Tool
At a large aerospace corporation in the Southeast, the CM manager turned in a recommendation to purchase a CM automated tool that would satisfy all requirements identified by the CM groups. Management delayed acting on the recommendation to give the other engineering departments time to review the recommended tool.
In the end, the recommendation to purchase the tool was cancelled. It was felt that while the tool did support the CM organization, it did not adequately address other developmental considerations that the engineering ranks felt were important. Sometime later a different tool was purchased, one that satisfied all the major requirements of SCM, the software developers, SQA, test, integration, and management organizations.
Overcoming Barriers to SCM
During a recent visit to a private-sector corporation (i.e., they did not deal with government contracts) in New England, it was discovered that the developer's major concern about implementing CM activities was all the restrictions they would have to deal with. They had been led to believe that CM meant formal controls, restricted access, limited ability to apply creative solutions, and so on. When it was suggested that data can transition to formally controlled baselines through a series of informal control steps, and that CM did not mean a lockdown and bottleneck, they became eager to be involved. After a number of meetings, a phased approach to formal CM allowed for the placement of informal controls and data gathering which led to baselined items. Everyone was pleased with the process.
The developers soon realized they could work together with CM as a team to solve problems rather than as two separate organizations with their own concerns and desired solutions. More importantly, perhaps, the CM group learned that when they got out of their corner office and out onto the engineering floor (being support and service oriented) they quickly became an integral part of the engineering and development process and team.
Implementing CM With an Electronic Database
A team of 35 to 40 developers was developing six computer software configuration items, which all had two or more customer variants as well as maintenance variants. The operating system was Unix, and the development languages were Ada, C, and C++. Implementing classical CM in this type of environment would normally require three to four CM practitioners to handle all the code and document manipulations. The team chose instead to implement a mostly developerexecuted CM system called Effective SCM . They implemented a Software Query Language-compliant, database driven, process oriented CM system, which supports a rule-based, closed-loop, changepackage approach to development.
Daily interaction with the CM system by the developers provided 100 percent tracking and status accounting of everything that happened to any file in the systems without the need for intrusion or interference by CM practitioners. The CM practitioners maintained the process model and performed the configured builds. As a result, CM support to this team was less than one person, and in fact was in the order of 80-120 hours per month instead of the more than 400 hours per month that a classical approach would have used.
The electronic database created by the engineers completely documented the execution of their software development plan. It also tracked the history of every file used in the system including change documents, baselines, and releases for each file. Note that rule-based, closedloop change control electronically implemented business rules that prevented the creation of a new version without authorization and prevented closure of a change request that had not been implemented.
A change-package approach supports electronic creation of new baselines by application of changes to a previous baseline. The tool electronically adds, replaces, or removes files that are related to the list of changes being made and is very effective in tracking development activities. (Note that Effective SCM is an unregistered trademark of BOBEV Consulting. For a complete description, see "Effective Software Configuration Management" in CrossTalk February 1998.)
Lessons Learned
The following are just a sample of the many lessons that have been learned from applying CM and its associated technologies.
The Importance of Planning
With only a few exceptions, if you look at any of the CM standards, manuals, guides, books, etc., you will likely find that CM has four major functions: (1) identification, (2) change control, (3) status accounting, and (4) auditing. In nearly every case, planning is left out. Yet, SCM is using much more complex equipment to establish and maintain complex environments, multiple baselines, multiple environments on multiple platforms, etc. Like everyone else, CM has to do all that faster, cheaper, smarter, and better than before. Planning has become more important than ever.
Planning cannot be interpreted as meaning a CM Plan has been written . That is certainly a good start, but much more is needed than just a document that explains SCM's roles and responsibilities. CM planning activities must also include, to name only a few, such things as the following:
- Metrics. How long? How many artifacts? When were they created? When were they updated? Where are they?
- Skill Mix. What is needed and who has it or who can get it?
- Infrastructure. Who is doing what, where, when, and how?
- Contingencies. If this happens, then what?
- Effort Tracking. Manpower levels.
- Subcontracts. Who has responsibility and authority?
- Resources. Budget, tool licenses, training, and head count.
- Matrix Management. Decentralized work force.
- Control Transitions. Informal to formal to field.
- Records Retention. What gets kept where and for how long?
- Control. Who controls what and how do they do it?
- Process. Standardized procedures for repeatability.
The most significant lessons are the following:
- Get an inside person on your side — an internal champion. They will become an evangelist for your solution to their co-workers.
- Get management buy-in and sponsorship. Management must really want it, not just go along with it. All levels of management need to support SCM. While implementing SCM, keep a focus on management sponsorship at all times.
- Maintain a sense of humor.
- Be flexible and sensitive to corporate culture.
- Seek out the early success.
- Do not use a critical project as pilot.
- Use a systems approach: Where am I? Where do I want to go? How am I going to get there?
- Success is more likely with lots of preparation, focus on CM and developer needs, breadth of participation, online access to sample process and planning templates, and standard terminology.
- Keep it simple. If it is too complex, or gets in the way, it will not get used.
- Communicate, communicate, communicate.
Learn'ilities' Services
Learn'ilities' provides consultancy services that enable organisations to succeed in their eLearning and eKnowledge objectives.
The range of services offered by Learn'ilities' is driven by the Learn'ilities' philosophy and experience. Organisations are now starting to move towards next generation IT systems in which they maintain the control and flexibility they require to meet their own business needs rather than being limited to the functions any single application or vendor can offer. While vendors can strive to maintain their own competitive advantages by what they do inside their 'black box' application, exposing the capabilities of their application as well defined services can allow organisations and consortia new flexibility in the way the reuse both data and content to provide the right types and levels of service to their clients and/or customers. Achieving this requires a strong focus on interoperability and reusability of both content and data between the various applications that participate in the overall system.
Learn'ilities' does not attempt to provide generalised approach to developing Service Oriented Architectures across a large enterprise or consortium. Learn'ilities' as the name suggests, is focused on the conceptual planning, development and implementation of the 'learning-focused' pieces of an architecture. This requires a focus on the Content Strategy of an organisation from an holistic perspective that includes the processes and practices that govern authoring, assembly, storage, maintenance, discovery, reuse and delivery of that content. In order to make this all work, the interrelationships between infrastructure, content and process must be 'in sync'. This specialist consulting on solutions for eLearning systems is the focus of Learn'ilities'. The diagram below illustrates the interrelationships and territory within which Learn'ilities' offers services.
The range of services offered by Learn'ilities' is driven by the Learn'ilities' philosophy and experience. Organisations are now starting to move towards next generation IT systems in which they maintain the control and flexibility they require to meet their own business needs rather than being limited to the functions any single application or vendor can offer. While vendors can strive to maintain their own competitive advantages by what they do inside their 'black box' application, exposing the capabilities of their application as well defined services can allow organisations and consortia new flexibility in the way the reuse both data and content to provide the right types and levels of service to their clients and/or customers. Achieving this requires a strong focus on interoperability and reusability of both content and data between the various applications that participate in the overall system.
Learn'ilities' does not attempt to provide generalised approach to developing Service Oriented Architectures across a large enterprise or consortium. Learn'ilities' as the name suggests, is focused on the conceptual planning, development and implementation of the 'learning-focused' pieces of an architecture. This requires a focus on the Content Strategy of an organisation from an holistic perspective that includes the processes and practices that govern authoring, assembly, storage, maintenance, discovery, reuse and delivery of that content. In order to make this all work, the interrelationships between infrastructure, content and process must be 'in sync'. This specialist consulting on solutions for eLearning systems is the focus of Learn'ilities'. The diagram below illustrates the interrelationships and territory within which Learn'ilities' offers services.
Learn'ilities' services:
- Solution Architecture for Integrated Learning Systems
- Infrastructure Planning, Application Selection
- Implementation Management
- Content Strategy Development
- content development guidelines
- metadata frameworks
- Workshop Facilitation
If you would like to find out how Learn'ilities' can help you with your eLearning needs then make your equiry via the Contact page.
Learn'ilities' Conceptual Approach
Strategy, Project Management, Implementation and Support Layer
Excellis brings best-in-class governance, business and technology consulting services to Global Track & Trace projects, providing end-to-end solution support, from strategy and compliance consulting to project management, implementation and support services. Our Global Track & Trace Solutions Practice focuses on improving client service, ensuring a secure supply chain, reducing cycle time and optimizing inventory management for Life Sciences and Pharmaceutical clients.
Excellis provides a focused and experienced perspective on Serialization and Track & Trace solutions, based on years of experience in the supply chain, providing guidance and leadership to large manufacturers, wholesalers, contract manufacturers, distributors, third-party logistics (3PL) and retailers. Our consultants can provide a full suite of services, from strategy to implementation to integration to configuration and program management.
- Global Serialization Strategy
- Track & Trace (ePedigree) Execution
- Packaging Line Automation
- ERP Integration
- DC Edge Technology
- End-to-End Program Management
Rapid changes in the global regulatory environment and local mandates are driving the need for serialized products in their supply chain. We offer Track & Trace expertise, including compliance strategy, serialization strategy, technology selection and systems implementation/integration services. Further, we have developed integration accelerators for all components, providing end-to-end Global Track & Trace solutions in record time.
Starting out small
Patch management can be a good starting point when trying to implement a more structured service management methodology within a small business. Jason Slater talks about the benefit of implementing aspects of service management frameworks in small business.
Small businesses operating with tight budgets and few IT personnel do not always have time to spend implementing structured methodologies as the business often needs to start trading as soon as possible and time needs to be prioritised addressing a never ending cycle of requirement analysis, sourcing, implementation, management, maintenance and disposal.
Small businesses operating with tight budgets and few IT personnel do not always have time to spend implementing structured methodologies as the business often needs to start trading as soon as possible and time needs to be prioritised addressing a never ending cycle of requirement analysis, sourcing, implementation, management, maintenance and disposal.
It can be difficult justifying, or even selecting, a suitable management framework, however, it is not always necessary to implement a full blown methodology and a smaller implementation can often be used as a stepping stone, acting as a proof of concept, whilst alleviating some problems and logically organising work flows and ensuring what needs to be done actually gets done. Of course, a number of formal methodologies are available to choose from and deciding which one is right for you could be a series of articles in themselves. However many of them aim to address similar issues but go about them slightly differently. What is consistent is that they offer logical, considered ways of achieving improvements through effective service management.
During busy or prolonged project periods smaller issues can sometimes be pushed down the pile of things to do, but these can have longer term impacts on productivity. A backup tape missed here, a patch missed there might not seem important at the time but are risks that can be better managed by implementing good working practices and a more structured way of working. You may discover that many of the actions you are already performing fit a particular service management function.
The idea of implementing a fully blown service management framework can be overwhelming at the outset. A brief glance through frameworks such as the IT Infrastructure Library (ITIL®) or the Microsoft Office Framework (MoF) and you might think your time is better spent actually solving problems than wading through paperwork - but spend a reasonable amount of time fire fighting and you may soon realise there must be a better way of working - and this has everything to do with operating a more structured methodology.
One of the important aspects of service management is what your customers think of you - from suppliers, through the user base to the board of directors - everyone is going to have a view of how you are performing and this may have little to do with the nuts and bolts of the operation but instead on how well you are serving the customer.
Someone once said the problem with IT is that if it is done well no one ever knows and having worked in a number of IT environments this is undoubtedly true. I do not recall ever being patted on the back for implementing a new SPAM control system or keeping the anti-virus software up to date but these are essential tasks and ones which will definitely be noticed if they do not get done.
Patch management is a function contained in service management frameworks that can be of great benefit to a small business and is often a good place to begin. Keeping up to date with software patches often starts out as installing whatever is required then rebooting the computer. But how do we ensure all client machines are using the same patch? How do we know if there is a patch we really need?
As time moves on we need to consider if patches can be applied consistently and we might need to ensure devices stay on if they are required - rebooting a device is not always convenient. Many things require patches including operating systems, office applications, and third party applications but other things require updates that fall into patch management including firmware updates and hardware drivers. The key point here is being able to keep the infrastructure up to date, be this for error fixing, security or software enhancements.
The first step in implementing structured patch management should always be a written policy setting down what you have, what needs to be done, who does what, how often it should be done, and any clarifications or limitations (often called a scope) that may need to be considered, in particular:
A list of equipment
For a large number of end points identifying the initial versions of software and firmware can be achieved using any number of network inventory tools available.
A list of who applies patches and when
It is important to focus on this area in particular. Consider whether users can install their own patches and make sure everyone understands which patches can be installed and which ones need consideration.
A list of authorised places to obtain patches
Keeping up to date on patches can be a hit and miss affair if not considered up front; it is often best to keep a list of all relevant and reliable information sources and check them regularly.
Set up a notification system for available updates and patches
A number of sites now offer email notifications of new patches and you should always keep up to date with patch information whether or not you decide to implement specific patches. Remember to always check the source of a patch before installing it - security is paramount, you can often also check the contents of the patch to ensure they arrive to you as expected - some vendors offer a checksum that you can use to verify the integrity of your patch prior to implementation.
A list of which patches and updates will be logged in a control document
Certain types of changes will benefit from being logged, though not all patches and software updates necessarily need to be logged, but in particular, drivers, firmware updates and server changes, as well as third party application changes should always be recorded. This log will help you analyse the problem should things go wrong.
Describe how a patch is implemented including any verification procedures
Know what to do if things go wrong
A word of warning, particularly for drivers and firmware updates. Always read the guidance notes associated with patches and software updates and always perform a backup routine before implementing any major software changes.
Patch priorities - for example, critical patches should take priority over software updates
Set review times for the guidelines to handle new requirements
Once written and agreed it is important to stick to this policy; once you start applying patches in an uncontrolled manner you start to drift away from the best practice you have laid down. If things start to drift away you need to reel them back in as soon as possible.
Information collected can be reported upon, showing number of patches, how many devices they were applied to and how much time was assigned to completing patch management tasks.
A successfully managed and operated patch management methodology will not only provide a more structured method for keeping software and hardware up to date, but can be used as a measure of performance, becoming a key performance indicator for the IT team and something the business can understand and appreciate.
Once patch management is under your belt you will be in a great position to look at other aspects of service management.
Cost Management Implementation Service
If your organization's projects are often cancelled due to uncontrolled spending or budgets being exceeded, your organization is in need of this RobustPMSM consulting service.
This service facilitates the planning and implementation of processes that enable effective management of project costs. To this end, RobustPMSM evaluates the corporation's existing project cost estimating and cost control processes and, where vulnerabilities are identified, will recommend specific improvements to both the processes and the associated technology.
In addition, the RobustPMSM Cost Management Implementation service facilitates the implementation of project cost management based on:
This service facilitates the planning and implementation of processes that enable effective management of project costs. To this end, RobustPMSM evaluates the corporation's existing project cost estimating and cost control processes and, where vulnerabilities are identified, will recommend specific improvements to both the processes and the associated technology.
In addition, the RobustPMSM Cost Management Implementation service facilitates the implementation of project cost management based on:
- The organization's method of accounting - i.e. "cash accounting", whereby cash flow of financial events is considered, or "accrual accounting", whereby economic activities (rather than cash flow) of financial events are considered.
- Cost categories - i.e. General Expenses, Capital Labor versus Expense Labor, Capital Purchases, etc.
change management - implementation
Managing the change
Preparation for change
– Resources
– Roles and responsibilities
Building the vision
Plan the change
• Devise appropriate strategies to introduce change
• Design the change
• Identify the significant steps in the change process
• Discuss the need for change and the full details of what is involved
• Allow people to participate in planning change
• Communicate the plan to all concerned
• Produce a policy statement
• Devise a sensible time scale
• Produce action plans for monitoring the change
• Allow people to participate in planning change
• Get all parties involved in and committed to the change
• Inspire confidence by forestalling problems and communicating regularly
• Devise a sensible time scale for implementation of change
• Anticipate the problems of implementation
• Understand why change is resisted
Implementing the change
• Check on and record progress
• Make sure that change is permanent
• Evaluate the change
• Improve on any weak areas
• Overcome resistance
• Involve all personnel affected
• Keep everyone informed
• Devise an appropriate reward system
• Be willing to compromise on detail
• Ensure that strategies are adaptable
• Select people to champion change
• Provide support and training
• Monitor and review
Two types of change
(1) Step change
(2) Incremental change
Step v incremental change
Techniques to help implement change
Teams building across units
Internal communication
Negotiation
Action planning
Change agents or champions of change
And a certain amount of compulsion manipulation and coercion
Change agents
Managers should be able to act as change agents:
Advantages of using a change agent:
Helping people to accept change
Six ways of overcoming resistance to change
(source: Kotter and Schlesinger In HBR 1979)
Monitor and review
Kotter’s change phases model
Change management failures
What not to do
Ways to increase resistance to change:
Managers can increase resistance by:
Reasons why change can fail
Eight common reasons for failure of change management:
(John Kotter)
Preparation for change
- Environmental analysis.
- Set out the strengths and weaknesses of the organisation
– Resources
– Roles and responsibilities
- Identify the change required
- Determine the major issues
- Identify and assess the key stakeholders
- Win the support of key individuals
- Identify the obstacles
- Determine the degree of risk and the cost of change
- Understand why change is resisted
- Recognize the need for change, identify current position, devise a suitable method
Building the vision
- Develop a clear vision
- Make it people clear about what a change involves and how they are involved in it
- What is involved
- What is the proposed change
- Why should we do it
- What the major effects will be
- How we can manage the change
Plan the change
• Devise appropriate strategies to introduce change
• Design the change
• Identify the significant steps in the change process
• Discuss the need for change and the full details of what is involved
• Allow people to participate in planning change
• Communicate the plan to all concerned
• Produce a policy statement
• Devise a sensible time scale
• Produce action plans for monitoring the change
• Allow people to participate in planning change
• Get all parties involved in and committed to the change
• Inspire confidence by forestalling problems and communicating regularly
• Devise a sensible time scale for implementation of change
• Anticipate the problems of implementation
• Understand why change is resisted
Implementing the change
• Check on and record progress
• Make sure that change is permanent
• Evaluate the change
• Improve on any weak areas
• Overcome resistance
• Involve all personnel affected
• Keep everyone informed
• Devise an appropriate reward system
• Be willing to compromise on detail
• Ensure that strategies are adaptable
• Select people to champion change
• Provide support and training
• Monitor and review
Two types of change
(1) Step change
- Dramatic or radical change in one fell swoop
- Radical alternation in the organisation
- Gets it over with quickly
- May require some coercion
(2) Incremental change
- Ongoing piecemeal change which takes place as part of an organisation’s evolution and development
- Tends to more inclusive
Step v incremental change
Techniques to help implement change
Teams building across units
Internal communication
Negotiation
Action planning
Change agents or champions of change
And a certain amount of compulsion manipulation and coercion
Change agents
Managers should be able to act as change agents:
- To identify need for change
- Be open to goods ideas for change
- To able to successfully implement change
Advantages of using a change agent:
- Forces trough change
- Becomes the personification of the process
- Responsibility for change is delegated thus freeing up senior managers to focus on future strategy
Helping people to accept change
- Consider how they will be affected
- Involve them in the change
- Consult and inform frequently
- Be firm but flexible
- Make controversial change as gradually as possible
- Monitor the change
- Develop a change philosophy
Six ways of overcoming resistance to change
- (1) Education and communication - if people understand the needs for change and what is involved they are more likely to co-operate.
- (2) Participation and involvement - to encourage people to feel ownership of the change.
- (3) Facilitation and support - listening to the real concerns of people affected.
- (4) Negotiation and agreement - agreement and compromise if necessary.
- (5) Manipulation - e.g. “buying off” leaders of resistance.
- (6) Explicit and implicit coercion - threats where necessary but this is a high risk strategy.
(source: Kotter and Schlesinger In HBR 1979)
Monitor and review
- Adapt as necessary
- Recording and monitor the changes
- Measure progress against targets
- Have the desired results been achieved?
- Has the process been successful?
- How do those affected feel about the new situation?
- What might have been done differently?
- How can those not responding well to the change be helped?
- Sustain the change.- prevent any back sliding
Kotter’s change phases model
- Establish a sense of urgency
- Create a coalition
- Develop a clear vision
- Share the vision
- Empower people to clear obstacles
- Secure short term wins
- Consolidate and keep moving
- Anchor the change
Change management failures
What not to do
Ways to increase resistance to change:
Managers can increase resistance by:
- Failing to specific about a change
- Failing to explain why change is needed
- Not consulting
- Keeping people in the dark
- Creating excess work pressure
- Expecting immediate results
- Not dealing with fears and anxieties
- Ignoring resistance
Reasons why change can fail
- Employees do not understand the purpose or even the need for change
- Lack of planning and preparation
- Poor communication
- Employees lack the necessary skills and/ or there is insufficient training and development offered
- Lack of necessary resources
- Inadequate/inappropriate rewards
Eight common reasons for failure of change management:
- Allowing too much complexity
- Failing to build a substantial coalition
- Failing to understand the need for a clear vision
- Failure to clearly communicate that vision
- Permitting roadblocks against that vision
- Not planning for short term results and not realising them
- Declaring victory too soon
- Failure to anchor changes in corporate culture
(John Kotter)
Corporate Finance
- Indicative company valuation
- Assistance at business plan preparation
- Investment analysis and evaluation
- Financial management implementation
- Business restructuring
- Management Buy-Out / Buy-In assistance
- Finance raising assistance (equity, debt)
Example of Financial Management Implementation
Example of Financial Management Implementation - Financial Reporting
Example of Financial Management Implementation - Sales Reporting
Communication Management Implementation Service
If your organization's project services/products are often delivered behind schedule or are over budget due to a lack of performance information being communicated to appropriate resources, therefore not enabling timely corrections to be made, your organization is in need of this RobustPMSM consulting service.
This service facilitates the planning and implementation of processes that enable effective management of project communications. RobustPMSM evaluates the potential effectiveness of using a corporation's existing information technology to provide the mechanism/transport used to distribute project information and performance reporting. However, based on this evaluation, it may also recommend that the technology be updated.
Examples of technologies/tools that RobustPMSM regularly facilitates the implementation of include (but are not limited to):
This service facilitates the planning and implementation of processes that enable effective management of project communications. RobustPMSM evaluates the potential effectiveness of using a corporation's existing information technology to provide the mechanism/transport used to distribute project information and performance reporting. However, based on this evaluation, it may also recommend that the technology be updated.
Examples of technologies/tools that RobustPMSM regularly facilitates the implementation of include (but are not limited to):
- Microsoft Project Server, Professional and PWA 2003/2007 and Microsoft Project and Portfolio Server 2007.
- Custom Views, Tables, Filters for Microsoft Project Server, Professional and PWA 2003/2007.
- Project Dashboards via Microsoft SharePoint Server 2003/2007 and SharePoint Services.
Change Management
The SAP system implementation will certainly have a deep and decisive impact on the organization and the personal working style in the company. Unless you can control such impact, the new business process and the new system will not be effectively adapted and used and eventually, the objectives of the system implementation may not be realized. In order to diminish these implementation risks, change management tasks intend to the synchronize system implementation with change management.
Implementation, Training, and Management Oversight
Due to the many changes that are inherent in implementing FlexChoiceRN, effective training, support and management are essential to a successful program. Our consultants will be on site during the crucial run up to “Go Live” and begin to become a part of the day-to-day operations team. Re -working processes, providing on going one-on-one training, and delivering key updates to Senior Management are all part of the hands on approach that FlexChoiceRN brings to the implementation. While many of the obstacles to success can be anticipated, there are always challenges that arise. Our consultants deliver the support, confidence, vision and expertise to overcome any challenges that stand in the way of a successful implementation. By taking a collaborative approach, our consultants work with you to ensure that there is effective communication at all levels and a clear understanding of any new policies and procedures.
After ”GoLive”, the FlexChoiceRN consultants remain in the role of providing day-to-day management oversight, and provide valuable feedback to Sr. Management. Our consultants will begin to track and deliver key reports that will assess the level of success that the program has achieved. By remaining engaged, providing ongoing support and delivering crucial outcomes information, our consultants stand behind the program in order to verify that measurable results are being met. Should changes need to be made, or improvement initiatives implemented, FlexChoiceRN consultants will remain involved and on site until the program is delivering sustainable results and achieves a level of stability that is satisfactory to the client.
After ”GoLive”, the FlexChoiceRN consultants remain in the role of providing day-to-day management oversight, and provide valuable feedback to Sr. Management. Our consultants will begin to track and deliver key reports that will assess the level of success that the program has achieved. By remaining engaged, providing ongoing support and delivering crucial outcomes information, our consultants stand behind the program in order to verify that measurable results are being met. Should changes need to be made, or improvement initiatives implemented, FlexChoiceRN consultants will remain involved and on site until the program is delivering sustainable results and achieves a level of stability that is satisfactory to the client.
Subscribe to:
Comments (Atom)